Scott Foote, CEO of Protinuum based in the United States participates in Risk Roundup to discuss Cyber-Security Risk Intelligence.
Cyber-Security Risk Intelligence
When security risks from cyberspace, merge and converge with geospace and space; security risk intelligence has never been more important for humanity than it is now in a digital global age. With millions of annual cyber-attacks, cyber-crime has become a real threat to individuals and entities across nations: its government, industries, organizations, and academia (NGIOA) using computers, smartphones, tablets, the internet of things, and other gadgets connected to the internet. Either somebody’s identity is stolen every few seconds, or someone’s confidential data is stolen as a result of cybercrime. This is a serious cause of concern.
Irrespective of cyberspace, geospace, or space (CGS), security risk intelligence has become one of the most important of the core elements which must be established by entities across NGIOA. It is no surprise that nations: their government, industries, organizations, and academia (NGIOA) are spending enormous resources on the gathering and analysis of cyber-security risk intelligence.
Today, more than ever, cyber-security risk intelligence must provide information that can be acted upon by NGIOA decision-makers, if it is going to be deemed of value in cyberspace, geospace, and space. Having said that, it is one thing to gather security risk data and extract information but an entirely different thing to turn that information into meaningful and actionable intelligence.
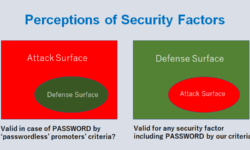
- Understanding Cyber-Security Risk Intelligence
- Defining Cyber-Security Risk Intelligence Goals
- Reliability of The Current Cyber-Security Risk Management Framework
- Cyber-Security Risk Intelligence Approach
- Cyber-Security Risk Intelligence Sharing
- Cyber-Security Risk Intelligence Programs
Interconnected and integrated CGS risk intelligence, needs to play a central role in CGS Security Risk Intelligence. Time is now to talk about cyber-security risk intelligence!
For more please watch the Risk Roundup Webcast or hear the Risk Roundup Podcast
About the Guest
Scott is a senior high-tech executive with more than 30 years of experience in cybersecurity and the broader software industry; serving both the public and private sectors. His primary area of expertise has been information security since the late 1980s; however, Scott’s technical experience ranges from operating system kernel technologies to the gamut of filesystem/database and info storage, to network engineering, to packaged commercial applications such as SCADA, B2B, and CRM solutions. His management experience spans the product lifecycle, with a specific focus on complex systems engineering and solution roadmap planning – including operational prototyping, rapid-growth product evolution, market adaptation, derivative product strategy, and next-generation rollout and migration. Since 1995, he has helped to launch or successfully re-invent over a dozen small businesses. Scott is a frequent guest speaker at industry events, sits on a number of advisory boards, and has been a member of the board of directors for enswers, Inc., Axixa Corporation, Realocity, Inc., Protinuum, LLC, and the Boston Affiliate of the Susan G. Komen Breast Cancer Foundation.
About Risk Group
Risk Group is a leading strategic security risk research and reporting organization.
Copyright Risk Group LLC. All Rights Reserved




 Asymmetrical Hybrid Warfare
Asymmetrical Hybrid Warfare