Christopher Frenz, Director at Interfaith Medical Center based in the USA, participates in Risk Roundup to discuss Medical Device Security Risks.
Medical Device Security Risks
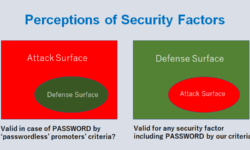
Medical devices are increasingly getting connected to the internet, hospital networks, and other medical devices. As a result, just like any other connected computer system, medical devices are also becoming vulnerable to security breaches from cyberspace, geospace, and space (CGS).
While the on-going breaches potentially impact the safety, security, and effectiveness of medical devices, it also brings to light the developing fear and mistrust towards the hospitals. When human lives are at the center of this rapidly evolving vulnerable healthcare ecosystem, understandably, the security of medical devices becomes a significant risk management concern.
As healthcare is on its way to becoming the largest attack surface for cybersecurity warfare, the big question is where would this end and what can be done? As we evaluate the medical device security risks, the concerns that in the coming years we, the humans, with our limited human intelligence, will not be able to secure medical devices surrounding us by just our efforts, is getting very real.
Now is the time to evaluate medical device security risks.
For more please watch the Risk Roundup Webcast or hear Risk Roundup Podcast
About the Guest
 Christopher Frenz is the Director at Interfaith Medical Center and focuses on healthcare information security and privacy. He has authored 2 computer books and over 75 technical articles.
Christopher Frenz is the Director at Interfaith Medical Center and focuses on healthcare information security and privacy. He has authored 2 computer books and over 75 technical articles.
The OWASP (Open Web Application Security Project) “Secure Medical Device Deployment Standard” and “Anti-Ransomware Guide” are some of his notable publications.
About Risk Group
Risk Group is a leading strategic security risk research and advisory organization.
Copyright Risk Group LLC. All Rights Reserved




 Blockchain Revolution – Risks & Rewards
Blockchain Revolution – Risks & Rewards