Humans are pattern seekers and pattern trackers, and from patterns, we derive meaning. If we can’t track cyber warfare patterns, how well will we identify the survival and security risks coming our way?
Introduction
Along with geospace, aquaspace, and space, cyberspace is now a contested common, and its use as a digital battleground to wage digital warfare is rapidly strengthening. This rapidly shifting landscape of warfare — where emerging cyberweapons have become more deadly than real battlefield weapons — is becoming a cause of great fear.
Keeping up with the rapidly intensifying complexity of uncontrolled warfare in cyberspace is a challenge facing not only for nation’s military but also individuals and entities across nations: its government, industries, organizations, and academia (NGIOA).
We must evaluate the ongoing cyber warfare as it becomes integrated with artificial intelligence (AI) and facial recognition technology. Considering its scope of overall entanglement with geospace, aquaspace, and space, the facelessness of enemy soldiers in the cyber domain, and the leveling of attack capabilities, we are entering an era where it seems a new model of cyber warfare governance is required.
Acknowledging this emerging reality, Risk Group initiated a much-needed discussion on “Cyber Warfare” with, Retired Colonel Prof. (Dr.) Don Welch, the Chief Information Security Officer, and Acting CIO and VP for Penn State on Risk Roundup.
Risk Group discusses Cyber Warfare with Retired Colonel Prof. (Dr.) Don Welch, the Chief Information Security Officer, and Acting CIO and VP for Penn State, an Affiliate Professor in the College of Information Sciences and Technology as well as the Department of Electrical Engineering and Computer Science based in the United States.
Cyberspace
Cyberspace is entirely human-made and has been designed, created, maintained, owned, and operated both by public and private stakeholders across nations. It is continually changing in response to technology transformation. Information, data, and electronic cargos are deployed instantaneously between any point of origin and any destination connected through the electromagnetic spectrum across CAGS. Since data and information travel in the form of multiple digitized fragments through unpredictable routings before being reconstituted at their destination, it brings many security vulnerabilities.
Warfare is not geographically rooted anymore. It has reached the contested commons of cyberspace and space. There is a vicious power struggle raging on in cyberspace. This new cyber battleground is full of unknowns, including major players, minor players, rules of war, and even reasons for war. In these cyber battlegrounds, the war casualties have been quietly piling up. It seems every NGIOA has been hit or is at risk of being hit. No one is spared, including common citizens. Is any nation prepared for this new warfare reality?
The rapidly transforming cyber battleground brings each NGIOA the good, the bad, and the unknown. With the world getting immersed in rapid advances in AI, facial recognition technology, and information, communication, and digitization technologies, the activities in cyberspace have become inseparable from activities in geospace, aquaspace, and space. It is becoming clear that conflict battlegrounds have changed fundamentally. So, how are nations reacting to the blurring boundaries of cyberspace with aquaspace, geospace, and space and the blurring battlefield in CAGS?
Understanding Cyber Warfare
Cyberspace is now a battlespace that we cannot see. Furthermore, its activities are hidden from the public eyes. Most knowledge of cyber warfare is intensely controlled, and the public would never know the reality of cyber warfare. The blurring boundaries of CAGS and growing threats from cyberspace mean that the cyber warfare challenges will perhaps need to be fought using more tools and resources than we currently have. Dr. Welch, Acting CIO and VP for Penn State proposed a need for a cyber militia on Risk Group: “Much like the colonial and early days of our nation where the Federal government was too weak to defend the frontier, we banded together to defend ourselves. We formed local militias who had the ability to defend themselves against those who wished them ill. We now must do the same thing. We must be able to defend ourselves because the U.S. Cavalry will not be riding to our rescue.”
This is especially relevant when NGIOAs work in silos. While large organizations have sufficient resources to defend their infrastructure, small organizations and individuals lack those resources. Moreover, we still do not have effective technologies and tools that will allow everyone to know that they are under attack or that they have been attacked. Cyber intelligence remains siloed and not shared. Acknowledging the growing need, Risk Group proposed a blockchain-based cyber-security risk management framework that would not only bring accountability in how we manage integrated security risks facing individuals and entities across NGIOA but also give us tracking capability of emerging security risks.
Furthermore, there is a growing concern about the democratization of warfare. How wars are fought and will be fought in the future are critical to understand. Who will fight the war, and what rules will govern the conduct of warfare. These must be clearly defined.
While humanity has survived many natural and some human-made existential risks for hundreds of thousands of years, the question today is whether humanity will survive the nature of the existing and emerging risks developing due to technology-triggered warfare in cyberspace, especially when the electromagnetic spectrum is itself being used as a war tool and is being weaponized. EM Warfare is a growing risk. (For further reading on EM warfare, please see The Weaponization of the Electromagnetic spectrum.)
Artificial Intelligence is Weaponizing Cyberspace
When the threats posed by cyber warfare are fought with AI, facial recognition technology, computer code, connected computers, the internet, information, and communication technology, and when highly sophisticated AI programs are already being used to control or destroy enemy systems, it is perhaps fair to say that NGIOAs are already in the middle of a vicious cyber arms race which is very complex and probably beyond human intelligence capability to respond. Are we at a point where mere human intelligence will not be sufficient to manage the security risks facing nations? Are we reliant on machines?
Artificial intelligence is on its way to weaponizing cyberspace. Reports are emerging that autonomous warfare in cyberspace has already begun. As a result, developing autonomous cyber defense and offense capabilities will be necessary for the protection of the complex CAGS ecosystem. As we see AI capabilities starting to be incorporated and integrated into cyberwarfare, how important have those capabilities become for cyberwarfare?
It is crucial to understand how malicious code that includes AI and machine learning capabilities changes the cyberwarfare landscape. It seems cyber warfare soldiers are already leveraging machine learning, and cyber warfare is already becoming automated. From data gathering and assessment to identifying vulnerability and target determination for precise cyber attacks, the entire cyberwarfare process is becoming automated. The reality is that automation is on its way to becoming a core component of both cybercrimes, cybersecurity, and cyber warfare. That brings us to an important question: what should nations be doing now to prepare and protect themselves against AI-driven cyber warfare? Perhaps there is a need for an Algorithm Naming and Identification System to have a tracking capability of algorithms that can be used for war.
What Next?
Since from the perspective of evolution, survival depends upon our being aware of dangers in the environment, it is time we understand the cyber battlefield and the complex challenges of cyber warfare.
This is especially important because humans are pattern seekers and pattern trackers, and from patterns, we derive meaning. If we can’t track cyber warfare patterns, how well will we identify the survival and security risks coming our way? If we don’t accurately track cyber warfare trends and events, we will be increasingly susceptible to those who manipulate us for profit, politics, or power.
NEVER MISS ANY OF DR. PANDYA’S POSTS
Join here for a regular update.



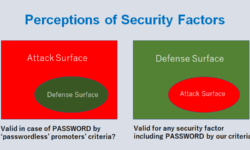
 Cyber Policy
Cyber Policy